|
|
Reservation, protection, understood, schemes, sharing, library.1. As computers become better … and more economical, every day brings new applications. 2. In an airline seat reservation system, a … agent might have authority to make reservations. 3. The airline example is one of … of corporate information for corporate self-protection. 4. It is convenient to divide protection … according to their functional properties. 5. These are systems that provide isolation of users, sometimes moderated by total … of some pieces of information. 6. In some cases the public … mechanism may be extended to accept user contributions.
8. Read the text and name the key points raised in it. Basic Principle of Information Protection
1) General Observations: As computers become better understood and more economical, every day brings new applications. Many of these new applications involve both storing information and simultaneous use by several individuals. The key concern in this paper is multiple use. For those applications in which all users should not have identical authority, some scheme is needed to ensure that the computer system implements the desired authority structure. For example, in an airline seat reservation system, a reservation agent might have authority to make reservations and to cancel reservations for people whose names he can supply. A flight boarding agent might have the additional authority to print out the list of all passengers who hold reservations on the flights for which he is responsible. The airline might wish to withhold from the reservation agent the authority to print out a list of reservations, so as to be sure that a request for a passenger list from a law enforcement agency is reviewed by the correct level of management. The airline example is one of protection of corporate information for corporate self-protection (or public interest, depending on one’s view). 2) Functional Levels of Information Protection: Many different designs have been proposed and mechanisms implemented for protecting information in computer systems. One reason for differences among protection schemes is their different functional properties-the kinds of access control that can be expressed naturally and enforced. It is convenient to divide protection schemes according to their functional properties. A rough categorization is the following. a) Unprotected systems: Some systems have no provision for preventing a determined user from having access to every piece of information stored in the system. Although these systems are not directly of interest here, they are worth mentioning since, as of 1975, many of the most widely used, commercially available batch data processing systems fall into this category ‑ for example, the Disk Operating System for the IBM System. Our definition of protection, which excludes features usable only for mistake prevention, is important here since it is common for unprotected systems to contain a variety of mistake-prevention features. These may provide just enough control that any breach of control is likely to be the result of a deliberate act rather than an accident. Nevertheless, it would be a mistake to claim that such systems provide any security. b) All-or-nothing systems: These are systems that provide isolation of users, sometimes moderated by total sharing of some pieces of information. If only isolation is provided, the user of such a system might just as well be using his own private computer, as far as protection and sharing of information are concerned. More commonly, such systems also have public libraries to which every user may have access. In some cases the public library mechanism may be extended to accept user contributions, but still on the basis that all users have equal access. Briefly, then, we may outline our discussion to this point. The application of computers to information handling problems produces a need for a variety of security mechanisms. We are focusing on one aspect, computer protection mechanisms ‑ the mechanisms that control access to information by executing programs. Finally, some protection designs can be evaluated by comparing the resources of a potential attacker with the work factor required to defeat the system, and compromise recording may be a useful strategy.
9. Read the following statements and say whether they are true or false. Correct the false ones. 1. Computers become more economical and bring new applications. 2. These new applications involve only storing information. 3. Different functional properties is the reason for differences among protection schemes. 4. Protection schemes are not convenient to divide according to their functional properties. 5. Every system has provision for preventing a determined user from having access to every piece of information stored in the system. 6. All-or-nothing systems have no public libraries which are accessible to every user.
10. Using information of paragraph 2 speak about a reservation system.
11. Make an outline of the text.
12. Make a short summary of the text in written form using your outline.
Part B
13. Look at the title of the text. Make your predictions about its contents.
14. Read the text and write out key words and phrases revealing the contents of the text.
15. Divide the text into logical parts. In each part find the key sentence.
16. Find one or two sentences which can be omitted as inessential in each logical part. Descriptor-Based Protection Systems
Descriptors have been introduced for the purpose of protecting information, although they are also used in some systems to organize addressing and storage allocation. For the present, it is useful to separate such organizational uses of descriptors from their protective use by requiring that all memory accesses go through two levels of descriptors. In many implementations, the two levels are actually merged into one, and the same descriptors serve both organizational and protection purposes. Conceptually, we may achieve this separation by enlarging the function of the memory system to provide uniquely identified (and thus distinctly addressed) storage areas, commonly known as segments. For each segment there must be a distinct addressing descriptor, and we will consider the set of addressing descriptors to be part of the memory system. Every collection of data items worthy of a distinct name, distinct scope of existence, or distinct protection would be placed in a different segment, and the memory system itself would be addressed with two-component addresses: a unique segment identifier (to be used as a key by the memory system to look up the appropriate descriptor) and an offset address that indicates which part of the segment is to be read or written. All users of the memory system would use the same addressing descriptors, and these descriptors would have no permission bits ‑ only a base and a bound value. The unique identifiers used to label segments are an essential cornerstone of this organization. They will be used by the protection system to identify segments, so they must never be reused. One way of implementing unique identifiers is to provide a hardware counter register that operates as a clock (counting, say, microseconds) and is large enough never to overflow in the lifetime of the memory system. The value of the clock register at the time a segment is created can be used as that segment's unique identifier. As long as the memory system remembers anything, the time base of the clock register must not be changed. Since the addressing descriptors are part of the memory system, which is shared by all processors, the system address space is universal. Any single processor address space, on the other hand, is defined by the particular protection descriptors associated with the processor and therefore is local. If the supervisor switches control of a real processor from one virtual processor to another, it would first reload the protection descriptors; the processor address space thus is different for different users, while the system address space remains the same for all users. With the addressing function separated architecturally from the protection function, we may now examine the two generalized forms of protection systems: the capability system and the access control list system.
17. Make questions to the text, interview your partner on the problems raised in it.
18. Express your attitude to the facts given in the text. You may use the following phrases: - it is full of interesting information … - I find the text rather/very cognitive… - I’ve learnt a lot … - I don’t agree with…
19. Say which facts presented in the text you’ve already been familiar with.
Part C
20. Read the title of the following text. Make your predictions about the contents of the text.
21. Read the text and find out the topical sentences in each paragraph. The Personal Information Protection and Electronic Documents Act
The Personal Information Protection and Electronic Documents Act (abbreviated PIPEDA or PIPED Act) is a Canadian law relating to data privacy. It governs how private-sector organizations collect, use and disclose personal information in the course of commercial business. In addition, the Act contains various provisions to facilitate the use of electronic documents. PIPEDA was passed in the late 1990s to promote consumer trust in electronic commerce. The act was also intended to reassure the European Union that the Canadian privacy law was adequate to protect the personal information of European citizens. PIPEDA incorporates and makes mandatory provisions of the Canadian Standards Association’s Model Code for the Protection of Personal Information, developed in 1995. “Personal Information”, as specified in PIPEDA, is as follows: information about an identifiable individual, but does not include the name, title or business address or telephone number of an employee of an organization. The law gives individuals the right to know why an organization collects, uses or discloses their personal information; expect an organization to collect, use or disclose their personal information reasonably and appropriately, and not use the information for any purpose other than that to which they have consented. The law requires organizations to: - obtain consent when they collect, use or disclose their personal information; - supply an individual with a product or a service even if they refuse consent for the collection; - collect information by fair and lawful means; and have personal information policies that are clear, understandable and readily available.
22. Say what you have learnt about the PIPEDA.
Unit V Computer security Word list
Part A
1. Define the following words as parts of speech and give the initial words of the following derivatives. Management, impenetrable, configuration, deterministic, verifiable, assurance, capability, functionality, protection, correctness.
2. Find the words and phrases in paragraph 1 that mean the same. a) a system in a computer that helps all the programs in it to work; b) safe from and protected against damage and attacks; c) to keep someone/ something safe from harm, damage; d) measures taken in order to keep someone/ something safe from harm, damage.
3. Translate the following sentences paying attention to the words in bold type. 1. None of the top 10 clonemakers now sells computers that run the Macintosh operating system. 2. The new mainframe operating system I have personally approved is going haywire; the computer is down half the time. 3. We like fast computers, the latest operating system, software and expensive peripherals. 4. A company can protect information of this kind only so long as it is confidential to the business and not in the public domain. 5. The decision he reached was that existing computer hardware was not sufficiently powerful to cope with the problem. 6. But another factor is that instruction manuals that usually accompany new computer hardware and software are difficult to understand. 7. The belief that it would be possible to maintain old computer hardware in operational order for use by future historians is utopian. 8. Please supply a valid name and password. 9. This computer system gives the user the capability of accessing huge amounts of data. 10. Both computers had a 28, 800-baud fax modem, 16 megabytes of random-access memory and voice mail / speakerphone capabilities. 11. The company has spent millions of dollars replacing outdated computer hardware. 12. The market permits people to make decisions and to act without going through the impossible task of collecting all the relevant information.
4. Fill in the missing words:   ЧТО И КАК ПИСАЛИ О МОДЕ В ЖУРНАЛАХ НАЧАЛА XX ВЕКА Первый номер журнала «Аполлон» за 1909 г. начинался, по сути, с программного заявления редакции журнала... 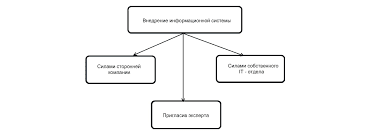 Что делает отдел по эксплуатации и сопровождению ИС? Отвечает за сохранность данных (расписания копирования, копирование и пр.)...  ЧТО ПРОИСХОДИТ, КОГДА МЫ ССОРИМСЯ Не понимая различий, существующих между мужчинами и женщинами, очень легко довести дело до ссоры...  Конфликты в семейной жизни. Как это изменить? Редкий брак и взаимоотношения существуют без конфликтов и напряженности. Через это проходят все... Не нашли то, что искали? Воспользуйтесь поиском гугл на сайте:
|